SPLIT EAS Anti-Shoplifting Device
Security experts say the most effective anti-shoplifting tools these days are tag-and-alarm systems, better known as electronic article surveillance (EAS) systems. Separately, these are good options. Used together, experts say, they're almost unbeatable. EAS is a technology used to identify articles as they pass through a gated area in a store. This identification is used to alert someone that unauthorized removal of items is being attempted. According to the Association of Automated Identification Manufacturers, over 800,000,000 EAS systems have been installed worldwide, primarily in the retail arena. EAS systems are useful anywhere there is an opportunity for theft of items of any size. Using an EAS system enables the retailer to display popular items on the floor, where they can be seen, rather than putting them in locked cases or behind the counter.
Get in Touch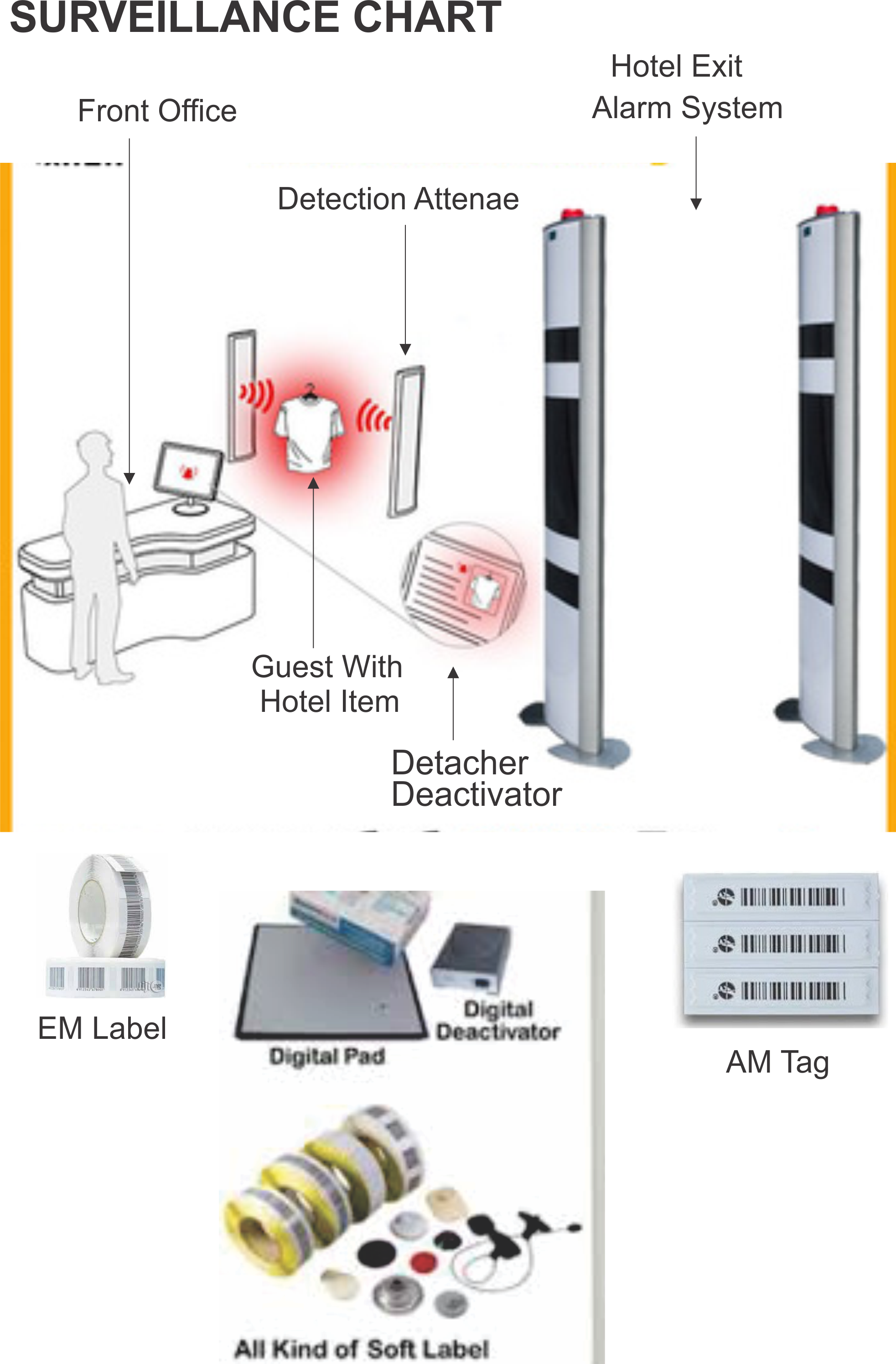
- KEY DIFFERENTIATOR
* 150+ technical expert resource pool
* Dedicated engineering labs for client’s products offering comprehensive security solution for their identity and authentication needs using smart-cards and tokens.
* QA & Testing Labs for data security products using strong encryption methods for protecting data of workstations and enterprise networks
* Expertise in TCP/IP stack, custom stack implementation, other LAN and Cellular Protocols
* Proven expertise on various Linux development and debugging tools like KGDB, gdb, etc.
* Strong capability in networking technologies – UDP, RTP, FTP, SMTP, IPsec, PPTP, ISAKMP, DHCP, PPPoE
Request QuoteBuilding Automation

And if you're someone who needs help conquering a pattern of shoplifting, please contact Shoplifters Anonymous. They can help!
Learn More
As a managed security services provider we are at the center of many corporations’ IT security operations. We tighten the matrix of technology, people, and processes by providing enterprise class, advanced security solutions to small and medium businesses. From security awareness training to multifactor authentication we are experts in IT security and can help your business mitigate IT security risks and employ the latest security technologies designed to safeguard your IT infrastructure and protect your business critical data.

Lorem ipsum dolor sit amet, consectetur adipisicing elit.
SERVICES
Network & Security
Rich experience on embedded devices, routers, Firewalls, NMS, IPS/IDS and expertise in writing device drivers/kernel modules on various Linux distributions (Ubuntu, Red Hat, OpenWRT etc.)
Learn MoreInformation Security
Experience on data security & integrity, expertise in the field of encryption using File System Filter Driver, Hardware Encryption and Cryptography.
Learn MoreRobotics & Automation
Proficiency in System Automation & developing real-time monitoring system, as well as, simulation and optimization of robotic operation for improved productivity & efficiency.
Learn More